🚀 We’re hiring – explore our open roles





















Your Trusted Source for Nx and Angular Expertise
Build performing and maintainable applications with top-tier consulting, thorough reviews, and specialized workshops from a global hands-on agency.
Our domains of expertise

Scalability
We future-proof your code to ensure smooth operations, no matter how much your business scales.

Maintainability
Good code is easy to read; great code is easy to maintain. We optimize your codebase for clarity, efficiency, and adaptability.
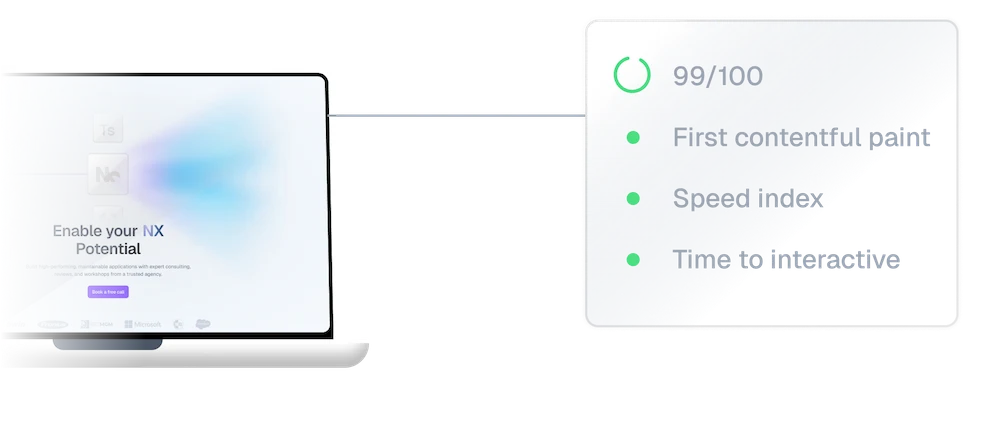
Web performance
Slow websites cost more than time—they cost users. PushBased.io specializes in identifying bottlenecks in your codebase and fix it.
Accessibility
We work with you to identify barriers, implement best practices, and create web solutions that embrace users of all abilities, making your website truly universal.
A service adapted to your needs
From individuals to large teams, we are able to help you thanks to a large set of solutions. We got you covered!
See us live 
At PushBased we do a lot of conferences in the world, let’s discuss in real life!











