Introduction to Ory
Table of Contents
Ory began as an open-source project in 2014, fueled by the vision to offer secure, scalable, and customizable authentication and authorization solutions. This commitment to open-source principles has propelled Ory into a vanguard position in the security landscape, providing a suite of tools designed to address the complex needs of modern applications.
Ory's Core Components and Features
Ory’s ecosystem relies on a foundation of open-source projects designed to protect modern applications with scalable and customizable authentication, authorization, and user management solutions. Each core component is developed with specific functionalities in mind, ensuring comprehensive coverage of identity and security needs.
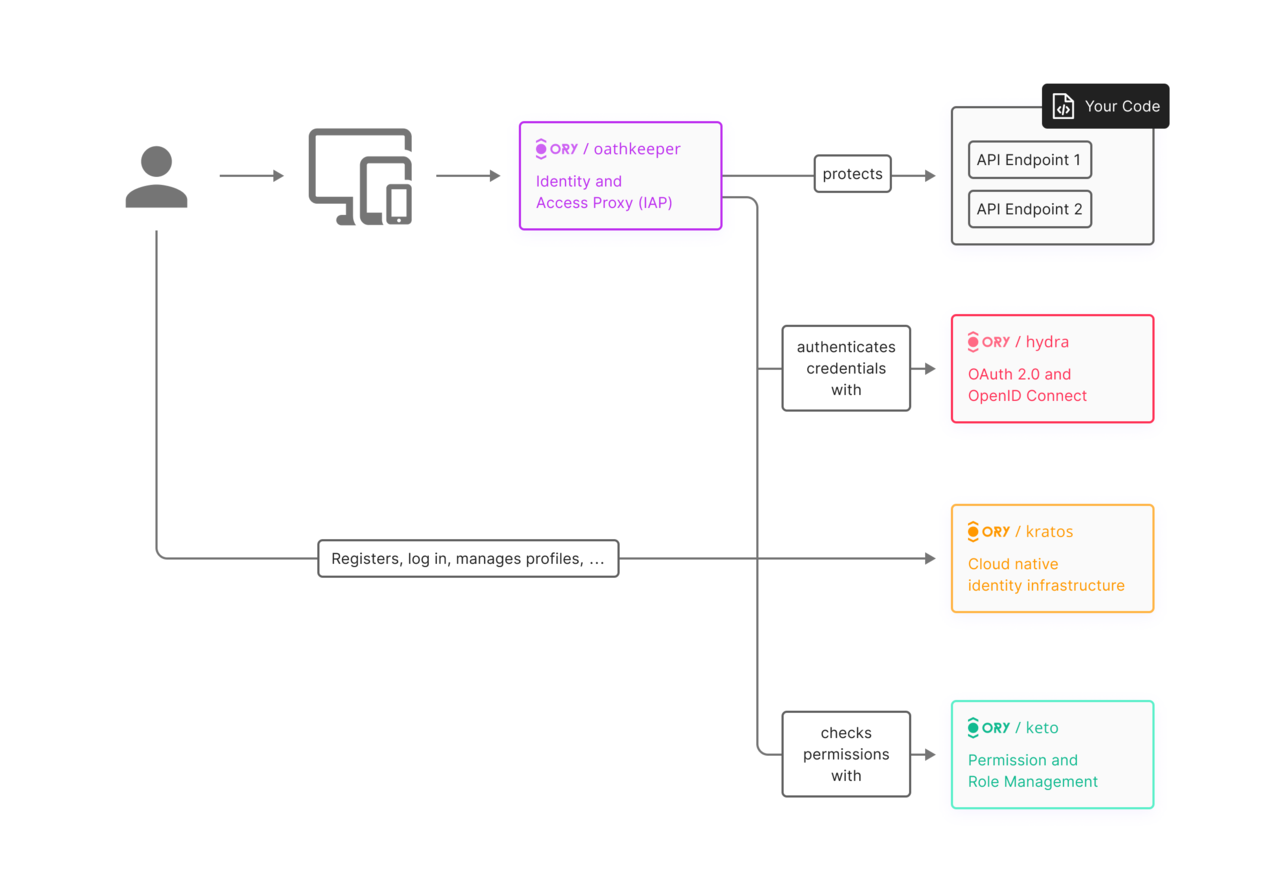
Disclaimer: The image above is an extract from the Ory official documentation.
Ory Kratos
AKA Ory Identities
Ory Kratos provides a robust identity management system that supports most authentication flows, such as login and logout, multi-factor authentication (MFA), account recovery, and passkey creation. The recent introduction of passkeys, a cutting-edge, passwordless authentication method, further underscores Ory Kratos's commitment to advancing user security and convenience. Beyond authentication, Kratos facilitates comprehensive account management features, such as profile editing, session management, and account activation and recovery, enabling developers to craft bespoke user experiences while ensuring the highest security standards. The self-service UI is a ready-to-use interface for managing user accounts and authentication flows.
The interactions between a browser-based client, a backend application, and Ory Kratos are typically structured as follows:

Note:
This flow is based on the Ory Kratos Self-Service Browser Flow a similar approach can also be adopted for Native Apps, Server-Side Apps, and CLI clients via the
endpoint. GET /self-service/<login|registration|settings|...>/api
Ory Keto
AKA Ory Permissions
Drawing inspiration from Google's Zanzibar, Ory Keto is a powerful authorization service using relation-based access control models (ReBAC). This approach enables fine-grained permission settings and dynamic access control policies, allowing developers to define complex hierarchies and relationships for secure and precise resource access management.
Relation Tuples encode policies, which describe the relationship between a subjectresourcerelation
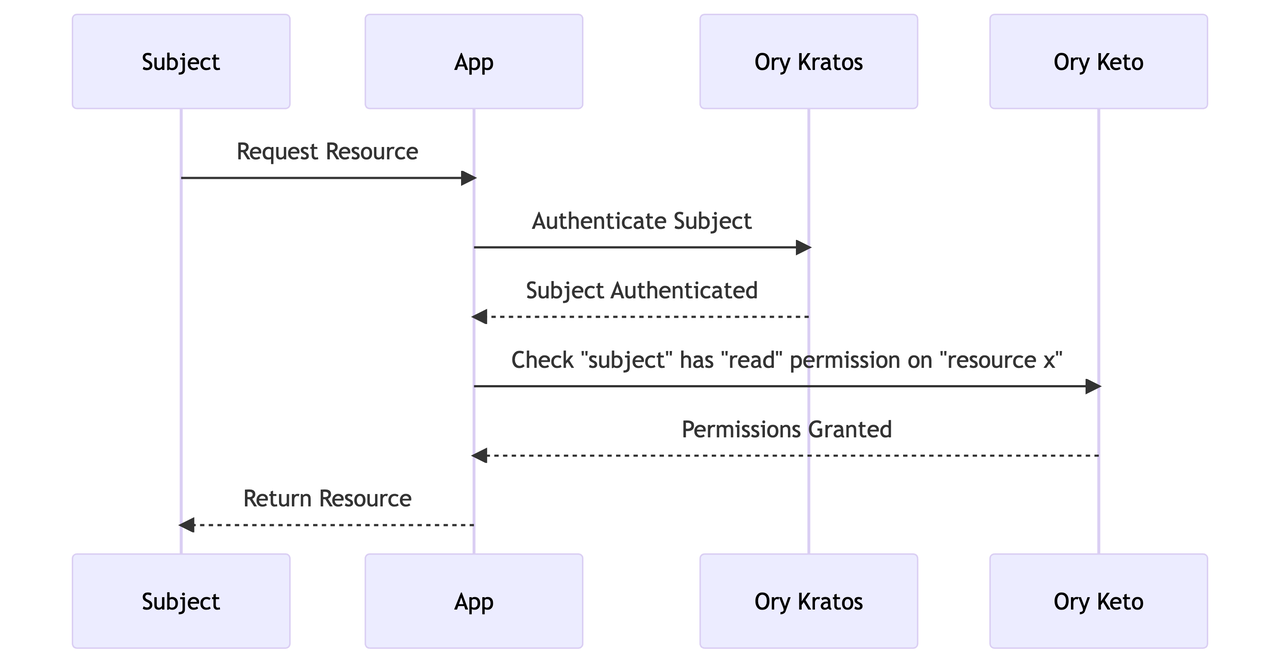
A typical interaction between a user, an application, Ory Kratos, and Ory Keto looks like this:
Ory Hydra
AKA Ory OAuth2 & OpenID
Ory Hydra is a secure token issuer and authentication provider specializing in OAuth 2.0 and OpenID Connect flows. It is engineered for high scalability and security, making it suitable for applications requiring robust client and application authentication mechanisms. Hydra supports client credentials flow and authorization code flow. It also provides a consent app for users to manage their consent.
The OAuth 2.0 flow between a client, resource owner, Ory Hydra, and resource server is depicted as follows:

Note: I left out Ory Oathkeeper as it might not be as relevant to the article's focus on authentication and authorization.
Ory Network: Bridging the Gap Between Open-Source and Cloud
Ory Network emerges as a seamless extension of Ory's open-source foundations, offering a cloud-based platform that enhances the Ory stack's capabilities. It emphasizes interoperability, allowing developers to leverage Ory's open-source projects while benefiting from the managed services and scalability of the cloud. This hybrid approach ensures that teams can maintain development agility and operational efficiency, regardless of their deployment preferences. Ory Network is thought and built for global accessibility and adherence to the most rigorous compliance standards.
Global Multi-Region Architecture: With a forward-thinking architecture, Ory Network ensures seamless tenant availability across multiple regions, eliminating the need for separate tenants per region. Read more about this architecture.
Commitment to Compliance: Recognizing the critical importance of data security and regulatory compliance for businesses, Ory Network conforms to the highest international standards, including ISO 27001, SOC2, and the General Data Protection Regulation (GDPR). This trio of compliance certifications showcases Ory's dedication to upholding stringent data protection and security policies.
Reliability: The reliability and scalability of an authentication and authorization solution are paramount, especially for applications with high user engagement. According to its status page, Ory Network has maintained an impressive uptime record, with a 99.99% availability rate over the past 12 months.
Tenant Management: Ory Network enables developers to create, configure, and organize tenants by workspace. This flexibility is particularly beneficial when working with multiple environments and teams.
Transparent Pricing Model: Ory Network's pricing model scales with user engagement without falling into enormous processing fees or hidden costs. The pay-as-you-go model is based on the number of active users and a set of features, ensuring cost-effectiveness and transparency.
Tips: See also Ory Network or self-hosting, which explains the benefits of Ory Network and self-hosting.
Integrating Ory into Backend and Frontend Applications
When transitioning to practical implementation, it becomes evident that Ory's design choices simplify integrating its services into both the backend and frontend layers of applications. Key features facilitating this integration include:
Extensive Documentation: Ory's commitment to a superior developer experience is evident in its rich documentation, guides, examples, and tooling, all aimed at facilitating integration.
Webhooks: Unlike Auth0's Actions, Ory Actions employs webhooks to integrate authentication events with your backend applications, enabling custom workflows and logic.
Account Experience: Ory provides a comprehensive set of self-service UI and API features for account management, including user creation, profile editing, and sign-in/out processes.
UI Components: Ory's UI components enable React developers to quickly integrate authentication features into their applications and create a unified user experience.
SDKs: Developers can utilize libraries generated from Ory's OpenAPI specifications, ensuring easy and consistent integration across different programming languages.
CLI Tools and Configuration Files: Ory built a CLI tool for individual resource management and configuration files for applying changes locally or to remote tenants, streamlining the configuration and deployment process.
Flexibility in Deployment: The ability to interchangeably use self-hosted solutions and cloud services underscores Ory's flexibility, accommodating varying deployment strategies and requirements.
This focused exploration of Ory highlights its strengths as a comprehensive solution for modern authentication and authorization challenges. In the following articles of this series, we will go through a hands-on journey to demonstrate how to integrate Ory's authentication and authorization solutions into your NestJS applications.
Some personal thoughts
Ory's hybrid approach emerges as a compelling choice, accommodating diverse project requirements and giving a sense of ownership and control over security infrastructure. Its open-source foundation, developer-friendly approach, and transparent pricing model that adapts to user engagement levels make it an attractive option for a broad spectrum of projects. Before committing to a solution, consider Ory Network’s free "Dev" plan to experience firsthand the benefits of its modern, scalable, and community-driven approach to security.
What I found particularly appealing:
Open-Source Foundation: Ory's commitment to open-source principles ensures transparency and community-driven innovation, as shown in Kratos and Keto contributions graphs.
Highly Customizable: Modify your email provider, use custom UI components, define your identity schema(s), and tailor authentication flows to your application's unique requirements.
Webhooks: Ory's (Kratos and Hydra) use of webhooks for authentication events enables seamless integration with backend applications, allowing for custom workflows and logic with any programming language or framework, and you can declare their configuration via the Ory CLI and the configuration files which makes it easy to replicate the production environment locally or in the CI runner.
End-to-end tests: it is super easy to use Ory locally or in the CI runner; spin some Docker containers with configuration files similar to the production environment.
User-friendly: Ory's documentation is complete, well-structured, and always up-to-date. Also, the Ory Network UI is slick and simple, keeping the noise minimal.
One area for improvement could be the complexity of the initial setup, especially for developers new to the ecosystem. Simplifying the onboarding process and providing complete guided tutorials could help users navigate the initial learning curve more smoothly. But I aimed to address this in this series of articles 😎.
